With BaseOne your business is ready for the information security and data privacy demands of modern organizations.

When you connect your environment to our SOC, we deliver advanced security coverage with centralized visibility across your systems. Every additional connection strengthens our ability to detect, analyze, and respond to threats in real time, providing:

Broader Coverage: With more endpoints connected, we can monitor a greater portion of your network, leaving fewer blind spots for attackers to exploit.
Improved Insights: A larger data pool enables us to identify patterns and anomalies faster, delivering smarter, more proactive threat responses.
Stronger Defense: More connections allow us to implement layered defenses and containment strategies more effectively, reducing risks across the board.
Uncover vulnerabilities in your applications, infrastructure, and systems
Uncover vulnerabilities in your applications, infrastructure, and systems
Uncover vulnerabilities in your applications, infrastructure, and systems
Uncover vulnerabilities in your applications, infrastructure, and systems
Uncover vulnerabilities in your applications, infrastructure, and systems
Uncover vulnerabilities in your applications, infrastructure, and systems

Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.
Continuous 24/7 security monitoring with immediate detection of threats and response to identified risks.

Our Incident Response retainer is a monthly subscription that gives your organization priority access to a dedicated team of experts—ready to respond immediately in the event of a cyberattack. This proactive arrangement ensures faster containment, reduces downtime, and limits the overall impact of security incidents.
Select the monthly Incident Response subscription that best fits your organization’s needs. Our plans scale to match your size, risk profile, and required response times.
Provide a few essential details about your business and environment so we can prepare your onboarding. You’ll get instant access to our Incident Response portal and emergency contact channels.
Once activated, you’re covered. Our team monitors for threats, stands ready 24/7 to respond to incidents, and keeps you informed with actionable updates—month after month.

Your organization isn’t truly secure just because a pentest was completed, 24/7 security monitoring is in place, or compliance with an industry standard has been achieved.
True security comes from doing what makes sense for your business—built on an integrated approach that builds trust with your customers and protects your organization while driving business growth.

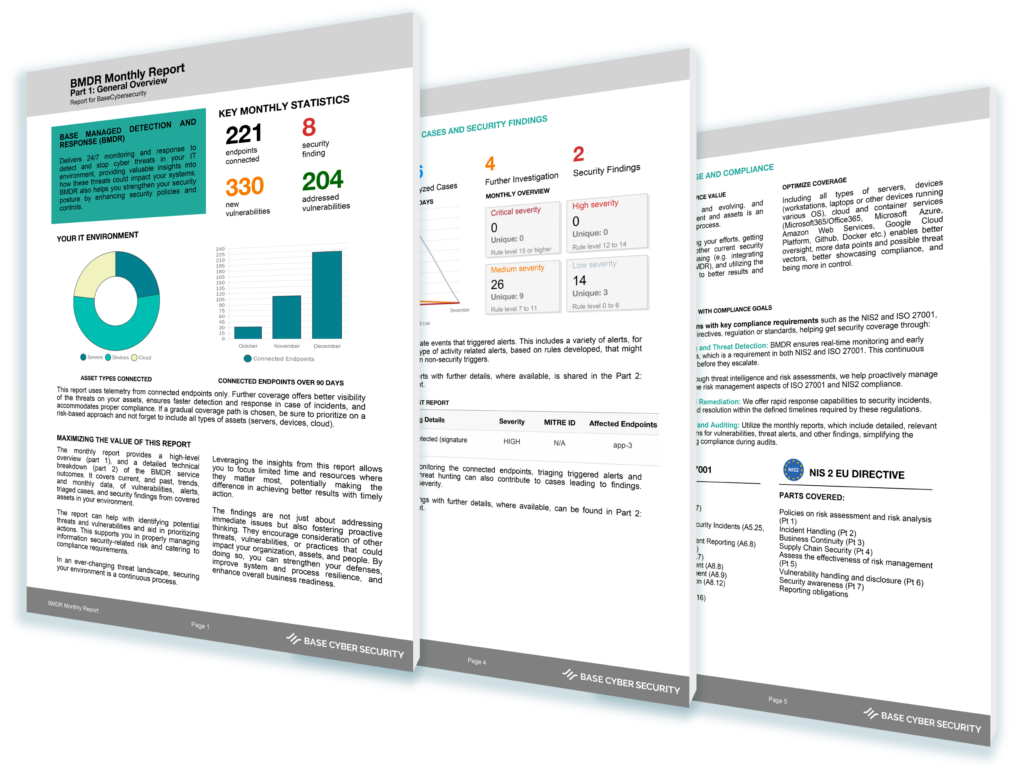
That’s any device used that may contain data about your company.
That’s any device used that may contain data about your company.
That’s any device used that may contain data about your company.
That’s any device used that may contain data about your company.
That’s any device used that may contain data about your company.
That’s any device used that may contain data about your company.
