
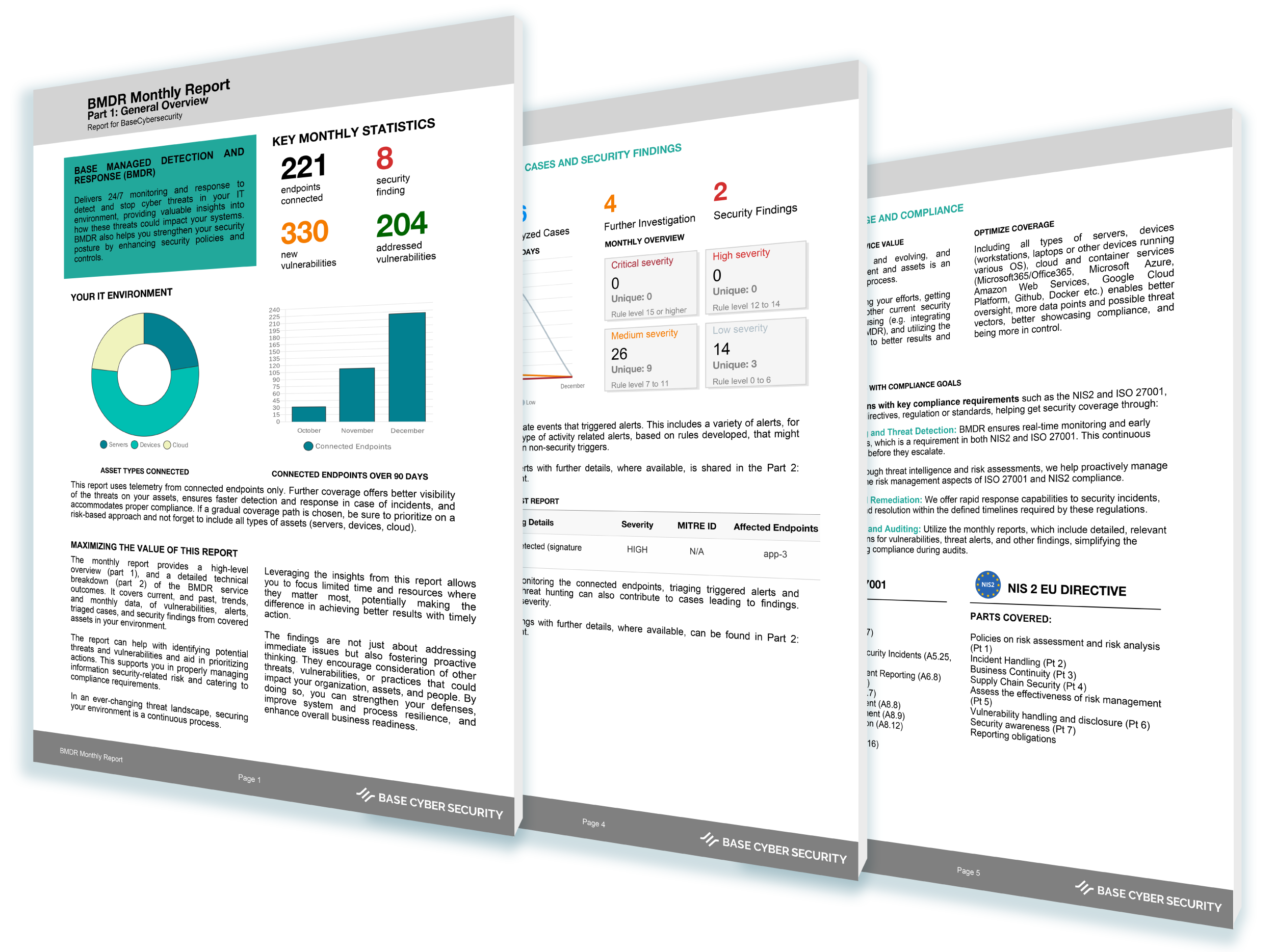
CEOs do not run their companies on yesterday’s numbers. They rely on live dashboards and ERP systems to see what is happening now, spot risk early, and act before small issues become costly ones. Cyber defense works the same way. When visibility is delayed, attackers move faster than decisions.
Modern threats unfold in minutes, not weeks. Without continuous insight into what is happening across your systems, security teams are always reacting too late. Real time visibility paired with immediate response turns security from a rearview mirror into a control panel, letting us detect abnormal behavior, contain threats instantly, and keep your business moving with confidence. In today’s environment, speed is not an advantage, it is a requirement.

24/7 Protection: Your environment is monitored around the clock, detecting and responding to threats, strengthening resilience and keeping your business prepared for the latest attacks.
AI & Human Protection: AI and humans collaborate to turn data pools into insight, allowing us to spot patterns and anomalies faster and deliver smarter, more proactive threat responses.
Maximum Protection: When you connect more assets we monitor a greater portion of your IT environment, leaving fewer blind spots for attackers to exploit and reducing overall risk.
Security teams are flooded with more alerts than humans alone can process. Our AI-powered defense platform combines the scale of AI with human driven decision making. We analyze massive volumes of security events in real-time, rapidly investigating what matters.
Continuous 24/7 security monitoring of your assets to identify risks and detect threats in real time
Identifies harmful files and behaviors early to stop attacks before they spread.
AI-improved accelerated analysis of high volume security events
Uncovers malicious software across systems and alerts you to potential infections.
Detects unusual user or system actions that may signal a threat.
Review of system settings to highlight weaknesses and misconfigurations that increase risk.
Actively searching for hidden threats that evade automated detection.
Shows you what attackers see, revealing exposed assets and vulnerabilities.
We take swift action when an incident occurs to contain damage and restore normal operations.
24/7 Monitoring and protection of Microsoft Cloud environments, including MS365 and Azure
24/7 security monitoring and threat detection for Google cloud environments, including Google Workspace and Google Cloud Platform.
24/7 security monitoring and threat detection for Amazon Web Services cloud environments.
24/7 security monitoring and threat detection for Linux server and endpoint environments


Connecting your systems to our Security Operations Center takes only a few minutes and gives you access to our expertise, while we maintain the unified security view behind the scenes. Our team continuously monitors your endpoints, servers, cloud services, and network activity from a centralized perspective, correlating signals across your entire environment to detect threats others miss.
As more systems connect, our visibility deepens and our response becomes faster and more precise. We continuously scan all internet facing assets and identify anomalies as they emerge, stopping threats before they escalate. By combining AI-enhanced automation with hands on security professionals, we move faster than attackers to stay ahead of both modern and legacy threats.
Protects systems from encryption attacks through continuous monitoring, rapid detection, and fast response.
Supports compliance by providing evidence of ongoing security oversight and risk management.
Identifies hidden risks through proactive investigation and continuous review of suspicious activity.
Finds unauthorized (or forgotten) apps and services to reduce unseen risks and improve overall visibility.
Delivers clear visibility into strengths and weaknesses across environment guiding improvement efforts.
Examines what occurred during an event, why it happened, and how to prevent a repeat.
Ensures essential operations can continue during unexpected disruptions through preparation.
Checks systems for weaknesses and highlights areas that need remediation before attackers find them.
Provides immediate action when a threat is detected to limit damage and restore normal activity quickly.

Our Incident Response retainer is a monthly subscription that gives your organization priority access to a dedicated team of experts—ready to respond immediately in the event of a cyberattack. This proactive arrangement ensures faster containment, reduces downtime, and limits the overall impact of security incidents.
Select the monthly Incident Response subscription that best fits your organization’s needs. Our plans scale to match your size, risk profile, and required response times.
Provide a few essential details about your business and environment so we can prepare your onboarding. We do a quick check to ensure telemetry is being received and you’re good to go.
Once activated, you’re covered. Our team monitors for threats, stands ready to respond to incidents, and keeps you informed with actionable updates—month after month.

It’s a 24/7 fully managed service that watches your IT environment for threats, identifies attacks early and helps stop them before they cause damage. You get security experts and smart technology working together to keep you protected.
Yes. Your environment is watched 24 hours a day, every day, so threats can be caught at any time.
Yes. When the system spots something suspicious, our security analysts check it, confirm if it’s a real threat and guide the right response.
Yes, we use AI to improve threat detection by automated pattern recogniation to detect unusual activity. It flags suspicious behaviour to our team of experts who can quickly take action, so that threats are caught earlier and with fewer false alarms.
We respond as soon as a threat is detected. Our team begins investigating right away and takes action to contain the issue as fast as possible.
We look for ransomware, malware, phishing attempts, suspicious user activity, cloud threats and other signs of an attack.
We alert you, contain the threat where possible and guide you step by step through what to do next. You’re never left to deal with an incident alone.
Pricing is simple and based on the number of devices or users you need protected. We can provide a clear number based on your Asset Selection.
Antivirus and EDR tools detect threats but don’t manage them for you. MDR adds expert monitoring, investigation and response support so threats are handled quickly and effectively.
